What Is the Difference between Vendor, Third-Party, Supplier, and Fourth-Party Risk Management?

Have you ever found yourself puzzled by the terms supplier, vendor, third-party, and fourth-party when it comes to risk assessment? You’re not alone. These terms are often used interchangeably in conversations about business operations and risk management, but they refer to distinct roles and require different approaches in risk assessment. Let’s break it down.
Imagine you’re in the manufacturing industry, producing high-end electronics. You’ll need raw material providers (suppliers), companies that deliver pre-assembled components (vendors), external service providers like IT support or logistics companies (third parties), and finally, the partners your logistics company might rely on (fourth parties). Consider the potential risks – what if your supplier delivers substandard raw materials, a vendor delays shipping essential components, a third-party IT provider faces a cyber-attack, or a fourth-party transportation service fails to meet delivery deadlines? This scenario highlights the critical importance of comprehensive risk assessment across all these relationships.
Understanding and managing these risks is key to keeping your business running smoothly, staying compliant, and maintaining trust with customers and stakeholders. But before we dive into the difference between Supplier, Vendor, Third-Party, and Fourth-Party Risk Management, let’s go over some basic terms.
Foundational Terms
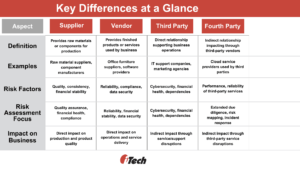
- First Party: This refers to your organization and the assets you control directly. For example, your company’s IT team managing your network infrastructure or your internal staff handling company operations. Essentially, these are the systems and resources your employees can access and manage directly.
- Second Party: These are your customers and their information systems. They engage with your company, providing compensation through money or data for your products or services. For example, customers buying your products or using your services, such as retailers’ shoppers or software companies’ users.
- Third Party: These are external entities with whom you have a direct relationship and upon whom your data’s confidentiality, integrity, or availability depends. They are not your employees or customers. Examples include:
- Contractors or consultants who help with specific projects.
- Suppliers providing raw materials or components.
- Service providers such as IT support, marketing agencies, or software vendors.
- Fourth Party: These entities do not have a direct relationship with your organization but are indirectly involved through your third parties. For example, if your logistics provider relies on a cloud service provider to manage their operations, it is a fourth party. Their performance can impact your business even though you do not interact with them directly.
Now that you understand the foundational terms, we can explore the difference between Supplier, Vendor, Third-Party, and Fourth-Party Risk Management.
Difference between Supplier, Vendor, Third-Party, and Fourth-Party Risk Management
Supplier Risk Management (SRM) / Supply Chain Risk Management (SCRM)
SRM involves managing risks from suppliers and the entire supply chain, including second, third, and fourth parties. It’s the most comprehensive discipline, ensuring risks from your customers’ actions, third-party providers, and fourth parties are managed effectively.
Key Elements of SCRM:
- Supply Chain Visibility:
- Mapping the Supply Chain: Identify all suppliers, including their location and role in the supply chain.
- Tracking Materials: Monitor the flow of materials from suppliers to your production line.
- Performance Monitoring: Regularly evaluate supplier performance through metrics such as delivery times and defect rates.
- Supplier Collaboration:
- Information Sharing: Share relevant information about demand forecasts, quality standards, and regulatory changes with suppliers.
- Joint Risk Assessments: Collaborate with suppliers to identify potential risks and develop mitigation strategies.
- Collaborative Problem-Solving: Work together to address issues and improve processes.
- Disruption Management:
- Diversifying Suppliers: Avoid relying on a single supplier by maintaining relationships with multiple suppliers for critical materials.
- Buffer Stock: Keep an inventory buffer to mitigate the impact of supply chain disruptions.
- Contingency Plans: Develop and regularly update plans to address potential supply chain interruptions, such as natural disasters or geopolitical events.
- Regulatory Compliance:
- Regular Audits: Conduct audits to ensure suppliers comply with industry regulations and standards.
- Compliance Checks: Verify that suppliers adhere to legal requirements and ethical standards.
- Adherence to Industry Standards: Ensure suppliers meet industry-specific guidelines and certifications.
Vendor Risk Management (VRM)
Vendors are third parties who provide goods or services directly to your organization, usually involving compensation. VRM focuses on managing risks related to these vendors.
Key Elements of VRM:
- Reliability and Quality Assurance:
- Regular Audits: Perform routine audits to ensure vendors meet your quality standards.
- Quality Checks: Implement quality checks at various stages of the vendor’s process.
- Performance Reviews: Conduct regular reviews of vendor performance and address any issues.
- Financial Stability:
- Financial Health Assessment: Review vendors’ financial statements, credit ratings, and market position.
- Risk of Bankruptcy: Evaluate the risk of vendors facing financial distress or bankruptcy.
- Market Position Analysis: Assess the vendor’s competitive position in the market and their ability to sustain operations.
- Compliance and Regulatory Adherence:
- Legal Requirements: Ensure vendors comply with relevant laws and regulations.
- Ethical Standards: Verify that vendors adhere to ethical business practices.
- Industry Guidelines: Check compliance with industry-specific guidelines and certifications.
- Data Security:
- Cybersecurity Measures: Ensure vendors have robust cybersecurity practices to protect sensitive information.
- Data Protection Policies: Review vendor policies on data protection and privacy.
- Incident Response Plans: Verify that vendors have plans in place to respond to data breaches or cyber-attacks.
Third-Party Risk Management (TPRM)
All vendors are third parties but TPRM includes a broader range of entities such as open-source developers and external service providers. TPRM manages risks related to these third parties who are not necessarily vendors.
Key Elements of TPRM:
- Due Diligence:
- Background Checks: Conduct thorough background checks on third parties.
- Review Past Performance: Assess third parties based on their history of performance and reliability.
- Risk Management Practices: Evaluate the risk management practices of third parties.
- Contractual Obligations:
- Clear Roles and Responsibilities: Define the roles, responsibilities, and expectations in contracts.
- Data Protection Clauses: Include clauses for data protection and compliance.
- Termination Conditions: Outline conditions under which the contract can be terminated.
- Continuous Monitoring:
- Regular Audits: Perform regular audits to ensure compliance with agreements.
- Performance Reviews: Conduct ongoing performance reviews of third parties.
- Real-Time Monitoring Tools: Use GRC tools to monitor third-party activities in real-time.
- Risk Mitigation Strategies:
- Contingency Plans: Develop contingency plans to address potential issues proactively.
- Alternative Solutions: Identify alternative suppliers or solutions in case of third-party failures.
- Collaborative Efforts: Work with third parties on risk mitigation strategies.
Fourth-Party Risk Management
Fourth parties are entities that do not have a direct relationship with you but impact you through your third-party vendors. Managing fourth-party risk involves extending your risk management to these indirect relationships.
Key Elements of Fourth-Party Risk Management:
- Extended Due Diligence:
- Assess Third-Party Partners: Conduct due diligence on third parties and their key partners (fourth parties).
- Identify Potential Risks: Identify risks that could affect your business through these extended relationships.
- Evaluate Impact: Assess the potential impact of fourth-party risks on your operations.
- Risk Mapping:
- Visualize Relationships: Create a risk map that includes fourth-party relationships.
- Identify Critical Points: Identify critical points of failure and dependencies in the extended supply chain.
- Understand Risk Landscape: Gain a comprehensive understanding of the extended risk landscape.
- Incident Response Planning:
- Develop Response Plans: Create plans to handle disruptions caused by fourth parties.
- Prepare for Scenarios: Prepare for various scenarios that could arise from fourth-party failures.
- Coordinate with Third Parties: Ensure third parties have incident response plans that account for their partners.
- Regular Assessments:
- Conduct Audits: Regularly assess fourth-party risks through audits and performance reviews.
- Monitor Changes: Continuously monitor changes or emerging threats in the extended supply chain.
- Update Risk Profiles: Keep risk profiles updated based on new information and assessments.
By understanding these key elements and how they differ across supplier, vendor, third-party, and fourth-party risk management, businesses can better prepare and protect themselves from potential disruptions and risks.
Conclusion
Understanding and distinguishing between these different types of risk assessments is vital. Tailoring your risk management strategies to each type ensures comprehensive coverage, business continuity, and regulatory compliance and maintains trust with your customers and stakeholders. So, next time you plan your business strategies, consider the various players involved and the potential risks they bring. A proactive approach to risk assessment can save you from many headaches down the road.
iTech GRC understands this and thus offers a comprehensive solution, ‘IBM OpenPages powered by Wastson.ai’, for managing these risks. With its advanced analytics, real-time monitoring, and integrated risk management capabilities, iTech GRC enables organizations to:
- Identify and Assess Risks: Quickly identify and assess risks across the entire supply chain and third-party ecosystem.
- Enhance Visibility: Gain complete visibility into direct and indirect third-party relationships.
- Ensure Compliance: Automate compliance checks and ensure adherence to relevant regulations and standards.
- Mitigate Risks: Implement effective risk mitigation strategies and contingency plans.
- Continuous Monitoring: Continuously monitor risk levels and performance metrics to stay ahead of potential issues.
Protect your organization from unforeseen disruptions and enhance your risk management capabilities with iTech GRC. Contact us today to learn how we can help you navigate the complexities of risk management and safeguard your business.
