Building a Robust Incident Response Plan for Third Party Risks like CrowdStrike: A Step-by-Step Guide

In our first blog of the series on CrowdStrike Resilience, we highlighted the crucial need for assessing third-party risks, particularly considering the recent CrowdStrike outage that disrupted several Fortune 500 companies. The outage served as a wake-up call, emphasizing the importance of continuous risk assessment and the potential consequences of relying on third-party vendors for critical cybersecurity solutions.
Now that you’ve completed your initial third-party risk assessment, it’s time to take your preparation a step further by strengthening your incident response plan. When a security incident occurs, every second counts. The faster your organization can respond, the better you can mitigate the impact. However, as the CrowdStrike outage demonstrated, even the best-prepared companies can face significant challenges if they lack a well-structured incident response plan. This is why it’s essential to have a plan in place that is not only comprehensive but also tailored to the specific risks associated with your third-party vendors.
So, in today’s discussion, we’ll guide you through creating a comprehensive incident response plan that ensures your organization is fully prepared to handle any potential security breaches, especially those related to third-party vendors like CrowdStrike. So, let’s begin!
A critical component of any effective incident response strategy is having the right tools and frameworks in place to manage IT risks and ensure compliance. This is where IBM OpenPages IT Governance solution comes into play.
IBM OpenPages IT Governance isn’t just about managing risks; it’s about aligning your IT controls with your business processes and ensuring that your organization is prepared to respond to incidents swiftly and effectively. This powerful module can be integrated into your incident response plan, providing you with the capabilities needed to manage IT-related incidents, analyze risks, and maintain compliance across various frameworks.
IBM OpenPages IT Governance: A Strategic Approach to Incident Response
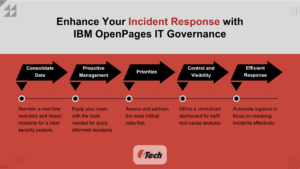
- Comprehensive Interoperability and Integration with third-party technologies
- Why It Matters: During a security incident, it is essential to have a unified platform that seamlessly integrates with various third-party technologies and internal systems. IBM OpenPages IT Governance offers robust interoperability through its REST API and IBM App Connect, enabling your organization to consolidate data from diverse sources, including enterprise infrastructure management applications. This integration is crucial for maintaining a real-time inventory of enterprise systems, importing security incidents, and providing a comprehensive view of your security posture across the organization.
- How It Supports Incident Response: By automating the management of security and regulatory requirements framework (e.g., NIST, UCF, ISO 27001) and integrating sophisticated Risk Quantification methods like RiskLens, OpenPages ensures that your incident response team has instant access to critical data and analytical tools. This capability empowers the team to respond quickly and effectively, minimizing the impact of incidents through informed decision-making and proactive management.
- Advanced IT Incident Analysis for Proactive Risk Mitigation
- Why It Matters: Effective incident response relies on the ability to analyze IT incidents in real time, identify root causes, and predict potential repercussions. IBM OpenPages IT Governance enhances this capability by providing tools that allow your organization to assess risks, measure the impact of incidents, and develop informed strategies to mitigate these risks. This proactive approach helps prevent minor incidents from escalating into major disruptions.
- How It Supports Incident Response: The platform’s integration across Incident Response, SecOps, and Risk teams ensures that all stakeholders have access to the same real-time data, facilitating coordinated efforts. This unified view enables quicker identification of vulnerabilities, better collaboration in developing containment strategies, and more efficient execution of incident response procedures, ultimately reducing recovery time and minimizing losses.
- Targeted Business Application Risk Assessment for Precision Response
- Why It Matters: Not all business applications are equally critical to your organization’s operations. IBM OpenPages IT Governance provides a framework for conducting detailed risk assessments on business applications, evaluating them against industry standards such as NIST, ISO, and PCI based on Confidentiality, Integrity, and Availability (CIA) requirements. This targeted assessment ensures that your response efforts are focused on the applications that matter most to your business continuity.
- How It Supports Incident Response: By mapping the identified risks and vulnerabilities directly to the business processes they support, OpenPages allows your response team to prioritize actions based on the criticality of each application. This targeted approach ensures that high-priority applications receive immediate attention, enabling your organization to maintain essential operations while addressing the incident.
- Centralized IT Governance Dashboard for Holistic Visibility and Control
- Why It Matters: During an incident, having a centralized source of information is critical for effective decision-making. The IT Governance dashboard in IBM OpenPages offers a customizable, comprehensive view of all active issues, incidents, vulnerabilities, and business applications. This holistic visibility ensures that nothing is overlooked, enabling your team to maintain control over the situation.
- How It Supports Incident Response: The dashboard’s drill-down capabilities allow your team to conduct root cause analysis swiftly, tracing issues back to their origin and identifying potential vulnerabilities that may have contributed to the incident. This capability accelerates resolution times and helps prevent similar incidents in the future by addressing underlying causes.
- Automated IT Incident Workflows for Efficient Incident Resolution
- Why It Matters: Time is a critical factor in incident response, and manual processes can slow down the resolution. IBM OpenPages IT Governance automates the notification, routing, and documentation of IT-related incidents, ensuring that every step of the response process is executed efficiently. Automation reduces the risk of human error and ensures that all necessary actions are taken promptly.
- How It Supports Incident Response: With automated workflows in place, your incident response team can focus on resolving the incident rather than managing the logistics of the response. This streamlined process not only speeds up the resolution but also ensures that all relevant data is captured and documented, providing valuable insights for post-incident analysis and continuous improvement.
Conclusion
Incorporating IBM OpenPages IT Governance into your incident response plan is a strategic move that enhances your organization’s ability to manage IT risks, respond swiftly to incidents, and maintain compliance with evolving regulatory requirements. By integrating its advanced capabilities with CrowdStrike’s cybersecurity framework, your incident response team will be well-prepared to tackle the complexities of modern cyber threats, ensuring your business remains resilient.
At iTech GRC, an IBM OpenPages premier partner, we specialize in helping organizations like yours implement and optimize these powerful tools. Our expertise ensures that your incident response strategy is robust, efficient, and aligned with your business objectives.
As we continue our series, the next we will guide you through the crucial steps to take within the first 24 hours following a security incident. So, stay tuned to keep your organization a step ahead in cybersecurity preparedness. Got any thoughts or questions? Drop a comment below or reach out to us; we’d love to hear from you!
