Role of a Risk Control Matrix in Ensuring GRC Compliance: A Complete Guide

Do not read this blog if you’re absolutely certain every risk in your business is perfectly under control. If every compliance step is flawlessly followed and there are zero gaps in your risk management, then skip this. But if you’re like most organizations, where even the most diligent teams sometimes miss critical details, keep reading.
According to a recent PwC survey, 81% of businesses that actively manage and quantify risks see improvements in productivity and gain more time for strategic initiatives. It’s clear that effective risk management isn’t just about avoiding problems. Rather, it is about creating opportunities for growth.
Let’s say your team is facing a regulatory audit and needs to prove that the right controls and safeguards are in place, or you’re addressing a cybersecurity concern with potential reputational impacts. Without a structured view of your risks, these situations can quickly rise into larger issues. This is where a Risk Control Matrix (RCM) becomes invaluable. An RCM offers a clear, organized view of the risks in your organization and how they’re managed, allowing you to respond effectively and stay ahead.
In this blog, we’ll explain what an RCM is, show you how to build and interpret one, and discuss how it integrates with a broader Governance, Risk, and Compliance (GRC) strategy. By the end, you’ll see how an RCM can simplify risk management, empowering your team to make proactive decisions and strengthening your organization’s resilience.
So, let us get started!
What is a Risk Control Matrix (RCM)?
A Risk Control Matrix, or RCM, is like your organization’s risk “cheat sheet.” It’s a tool that shows you, in one simple format, what risks you are managing and exactly how you are handling them. With risks listed on one side and controls on the other, it creates a clear link between each risk and the specific steps your team has in place to control it.
Here’s how it works: The RCM organizes risks into categories, such as compliance, cybersecurity, operational, or financial, and then assigns each risk a level of severity, like high, medium, or low. Alongside each risk, you’ll see the corresponding controls i.e. the actions or processes set up to prevent or mitigate that risk. For instance, a high-severity cybersecurity risk might have multiple controls, like regular audits or firewalls, to keep it in check.
By laying out all this information in one place, the RCM helps everyone on your team understand what’s being done to manage risks. It’s a powerful tool to stay aligned, make data-based decisions, and avoid letting any critical details slip through.
Next, we’ll learn how to actually create and interpret an RCM so you can put it to good use.
How to Build and Read a Risk Control Matrix
By following a few simple steps, you can build a matrix that effectively maps out risks and ensures your team knows how to manage them. Let’s break it down to keep things straightforward.
- Step 1: Gather Key Team Members: Start by bringing together leaders and key stakeholders from departments like finance, compliance, IT, and operations. Each area has unique insights into specific risks, so getting a wide range of perspectives is essential. For example, while finance might focus on budget risks, IT would know best about cybersecurity threats. This initial step helps you build a well-rounded understanding of the risks across your organization.
- Step 2: Identify and Categorize Risks: Once your team is assembled, work together to identify all relevant risks. Organize these risks into categories to make tracking easier. Here are some common categories to consider:
- Compliance Risks: Risks related to legal and regulatory requirements
- Cybersecurity Risks: Risks related to data breaches, malware, or unauthorized access
- Operational Risks: Risks that affect day-to-day business functions, such as supply chain issues
- Financial Risks: Risks that impact financial stability, such as budget overruns or missed revenue targets
Categorizing risks helps you see where they fit within the larger picture. This structure also allows for more effective planning and reporting.
- Step 3: Define Specific Controls for Each Risk: For each risk, identify the specific controls you have in place. Controls are the actions, processes, or tools you use to manage or mitigate each risk. Make these controls clear and specific. For example:
- For a cybersecurity risk like unauthorized access, a control might be – implement multi-factor authentication.
- For a compliance risk, a control could be – conduct regular training sessions on regulatory changes.
Ensuring each control is actionable and relevant helps make the RCM practical for day-to-day use.
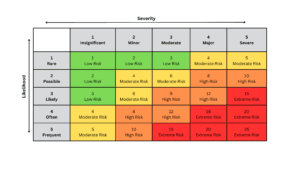
- Step 4: Assess and Score Each Risk: Now, it’s time to assess the severity and likelihood of each risk. This is where the matrix format becomes useful because it allows you to visualize the importance of each risk based on these two factors:
- Severity: This measures the potential impact of the risk if it occurs. Think of it in levels, like minor, moderate, or catastrophic. For example, a data breach that impacts thousands of customers would be a high-severity risk.
- Likelihood: This refers to how probable it is that the risk will occur. A five-point scale, with ratings from highly unlikely to highly likely, helps provide a clear view. For example, a risk with an 80% chance of happening would be rated as highly likely.
Assigning numerical values (like 1 to 5) to each factor lets you calculate a risk score by multiplying the severity and likelihood. This score gives you a simple way to prioritize risks. Higher scores indicate higher-priority risks that require more immediate or intensive controls.
- Step 5: Organize, Color-Code, and Document: Now, document each risk and its associated information in the RCM. Lay out your matrix by listing risks on one axis and controls on the other. For each risk, include:
- Risk Description: A brief explanation of the risk
- Severity and Likelihood: The assigned scores to show importance
- Controls: Specific actions in place to address the risk
- Owner: The person or team responsible for monitoring and managing the risk
Adding color-coding makes it visually easier to understand and prioritize risks:
- Green: Low-risk areas that may require only occasional review
- Yellow: Moderate risks needing regular monitoring and preventive measures
- Red: High-risk areas requiring immediate attention and stronger controls
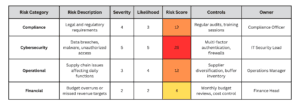
Reading the Matrix
Once your RCM is complete, it’s easy to read and interpret. Each row provides a clear view of a particular risk, the controls in place to address it, and its priority level. The color codes help you spot critical risks at a glance, so your team knows where to focus resources and efforts.
With this setup, your RCM becomes a valuable tool for ongoing risk management. You can easily update it as new risks emerge or existing risks change, ensuring it remains relevant to your organization’s needs.
Integrating the Risk Control Matrix (RCM) with GRC Processes
The Risk Control Matrix is more than just a standalone tool. It is a foundational element of a larger Governance, Risk, and Compliance (GRC) framework. Integrating your RCM with GRC processes can help streamline your organization’s risk management efforts and create a unified approach to handling risks.
Here’s how the RCM connects with various parts of a GRC program and enhances your risk management strategy:
- Control Mapping to Compliance Frameworks: Compliance frameworks often require that certain controls are in place to manage specific risks. The RCM provides a structured way to map your existing controls to these requirements, helping ensure you meet all compliance obligations.
By keeping your RCM aligned with compliance frameworks, your organization gains a clear view of where it’s compliant and where additional controls may be needed.
- Supporting Policy Management: Policies are essential to guide how your organization handles risks, and in many cases, these policies are themselves forms of risk control. Your RCM can link specific risks to policies, making sure each risk management measure aligns with established procedures. For instance, if you have a policy requiring employee training on data privacy, your RCM will show how this policy supports your cybersecurity risks.
This linkage between risks and policies simplifies monitoring and helps you maintain a consistent risk management approach across all departments.
- Enhancing Incident Response: An effective incident response process is vital for handling unexpected events, like a cybersecurity breach or a compliance issue. The RCM can play a key role in this process. When an incident occurs, you can quickly look at the RCM to understand which controls were in place, which ones failed or were bypassed, and what corrective actions are needed. This makes it easier to analyze the root cause and adapt your response.
Incorporating the RCM in incident response efforts also means your team has a clear record of risks and controls, allowing them to address vulnerabilities faster and prevent future issues.
- Streamlining Reporting and Analytics: With an RCM, you have a centralized source of data about your risks and controls. This information can feed into GRC reporting and analytics, helping you spot trends and evaluate control effectiveness over time. For example, if certain controls are consistently effective, this can guide resource allocation, allowing you to strengthen weaker areas. Similarly, patterns in risk scores can reveal emerging threats, which can then be prioritized.
Incorporating the RCM in your reporting processes not only makes your risk management efforts transparent to auditors and stakeholders but also supports data-driven decision-making across the organization.
- Facilitating Continuous Improvement: An RCM is not a one-time setup; it should evolve as risks change and new controls are implemented. Integrating the RCM into your GRC program ensures that it’s continuously updated, keeping pace with internal and external changes. For example, as regulations shift or new risks emerge, your RCM will adapt, providing a real-time view of your organization’s risk landscape.
By regularly updating your RCM, you create a dynamic risk management tool that strengthens every part of your GRC strategy.
Next Steps: Leverage RCM benefits with IBM OpenPages
Incorporating a Risk Control Matrix (RCM) into your GRC strategy is crucial for proactive risk management. IBM OpenPages simplifies and enhances your RCM efforts, offering customizable matrices to fit your specific business needs. It also provides flexibility to present reports in both quantitative and qualitative formats, giving you valuable insights for better decision-making.
So, reach out to iTech GRC today and take the next step toward a more resilient, well-managed risk environment.
