Rise of Social Engineering: Types of Social Engineering Attacks (Part 2)

After a prelude to the concept of social engineering as an emerging form of cybersecurity attack, let’s explore the different forms your enterprise may likely encounter.
First, let’s have a quick look at some stats on social engineering assaults:
- An average business encounters nearly 700 social engineering attacks annually.
- 50% of social engineering attacks are pretend incidents, in which threat actors create scenarios to convince victims to reveal sensitive data.
- About 90% of data breach incidents target human elements, as it is easier to trick employees into sharing confidential information to gain access to systems and networks than to surpass security firewalls.
- 86% of organizations have at least one employee who has clicked a phishing link.
From the above stats, we have established that social engineering attacks are frequent, maliciously well-planned, mainly leverage human vulnerability, and always target people. Below, we have identified some common types of social engineering attacks cyber criminals use.
Ten Common Types of Social Engineering Attacks
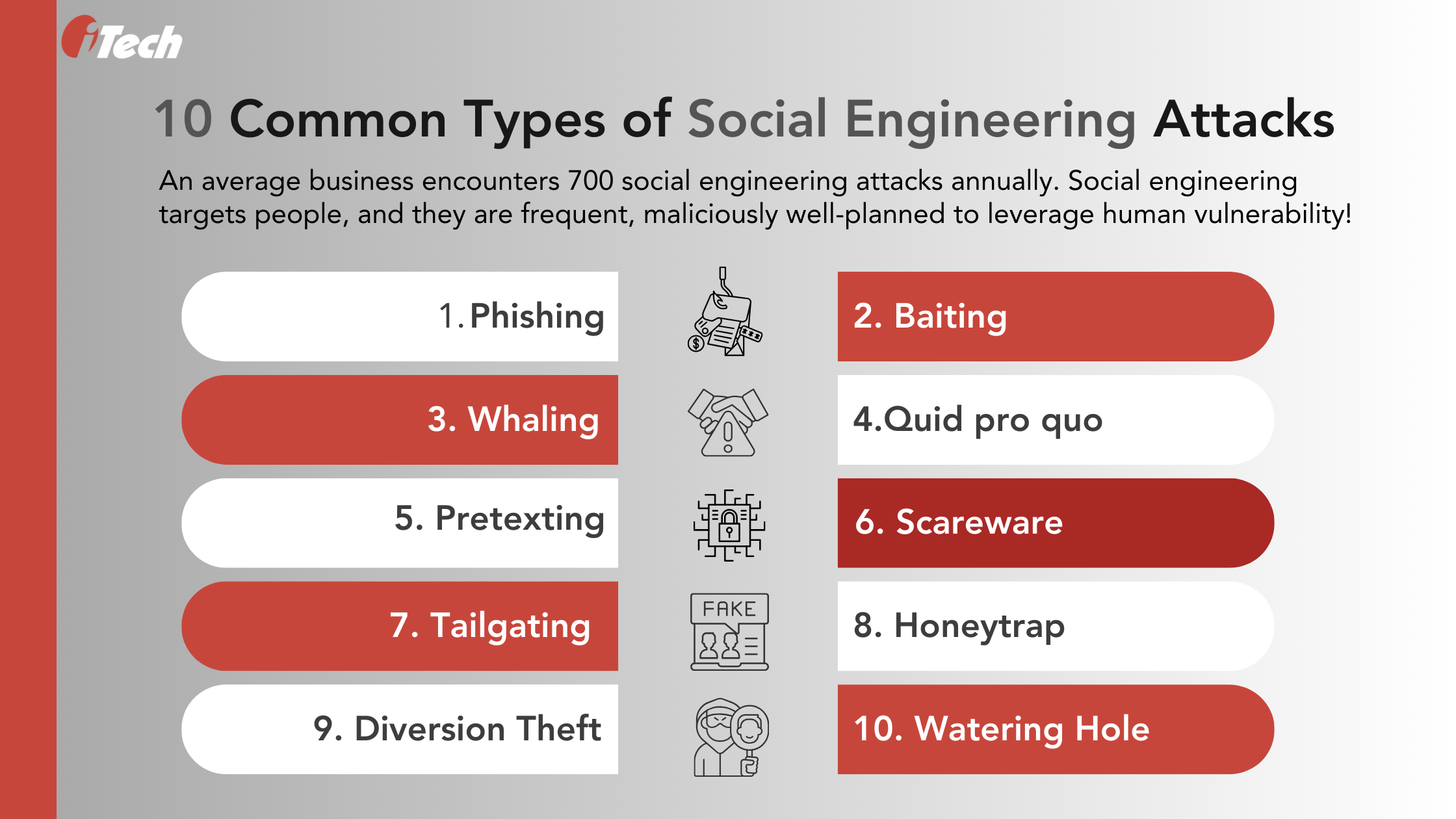
- Phishing: The most common cybersecurity attack is phishing. It involves enticing a target or users into clicking a suspicious link, downloading virus-infected files, or inadvertently revealing confidential information like email credentials, passwords, account details, etc. Phishing attacks can occur over emails, SMS, voice conferencing, and cloud-based file-sharing platforms. FBI’s 2020 Internet Crime Report found that phishing is a widespread cybersecurity crime in finance. According to Check Point Research, the technology industry is most vulnerable to brand phishing (hackers imitate leading brands), followed by shipping brands and social media networks. In 2022, hackers targeted victims, imitating brands like Yahoo, DHL, Microsoft, Google, Netflix, and HSBC.
- Baiting: As the term suggests, baiting involves luring victims with appealing messaging to download a file or click on a link to redeem gifts and offers. The links may redirect users to fake websites or a webpage that captures and shares login credentials with attackers. Baiting promises free software downloads or malware-ridden flash drives deliberately left in places that trigger victims’ curiosity to explore and fall prey to the attacks. Baiting scams include online forms, job application sites, and craftily labeled ads to entice users.
- Whaling: Whaling is a hyper-personalized attack targeting a particular user. Unlike phishing attacks that target millions of users, whaling involves outreach based on deep research on an individual’s social media activity, online persona, and other behavior. Whaling is generally targeted to individuals of high net worth or high-profile job roles to access confidential data that can be held for ransom.
- Quid pro quo: This attack implicitly solicits confidential data in exchange for a service. For instance, a cybercriminal can infiltrate a workplace and ask for an employee’s user credentials to resolve an IT incident. Then, the cybercriminal can leverage that information to access confidential data or sell it for ransomware.
- Pretexting: Pretexting is a different form of social engineering attack that convinces victims with believable scenarios or information to share valuable and confidential data. A pretexting incident can involve attackers posing as someone of high authority, like a law enforcement personnel or tax official, to earn their victims’ trust and gain the information they need.
- Scareware: Scareware is pop-up windows or alarming notifications about a virus download or other cybersecurity-related urgencies that can drive a victim to purchase anti-virus software or other tools to mitigate further risks and damage.
- Tailgating: Tailgating happens in the physical world, where attackers physically access or enter restricted spaces. For example, an individual can pretend to be an employee who has forgotten their identity card and convince security to allow them into a restricted place like an office or place of business.
- Honeytraps: Honeytraps are common on social networking platforms that involve virtually building a romantic relationship with victims to earn their trust and mislead them into revealing confidential information.
- Diversion Theft: Diversion thefts occur in both online and offline situations. In the online scenario, attackers can steal data from an employee over email by pretending to be someone working in the same organization.
- Watering Hole: Watering Hole targets websites and online platforms that target victims to visit or log in by adding their credentials. The attackers steal victims’ login details by infiltrating their network or through a trojan attack to access the network.
Social Engineering: Ten Obvious Giveaways
Social engineering delivery methods usually involve communication and messaging platforms that victims are known to use regularly or log in using credentials. Even though most of these cybercrimes look legit and convincing, there are red flags that help users identify a possible threat.
Cybersecurity research and facts based on survey reports reveal that the tactics social engineers use aren’t rocket science. All one must do is look closely, and clues are hidden in plain sight. Below are some of the essential social engineering giveaways that your enterprise can use to educate your workforce and avert costly human errors:
- The messages or offers are always too good to be true.
- Attackers usually know their victims well.
- Messages or communications soliciting information or money are immediate cybersecurity red flags.
- Real-life phishing emails have poor grammar and spelling errors.
- Compare URLs and links for safety and recognize malicious links.
- Most social engineering attacks have a pattern. For example, phishing emails have specific subject lines, and common attack vectors include links, PDF attachments, fake brand/business logos and names, and login landing pages.
- 91% of bait emails are sent via Gmail accounts, which are free to create and mostly reputable. However, one must be wary of what’s in the inbox.
- Emails with hidden threats have read receipts to inform attackers when the victims open the mail.
- Subject lines overdo the convincing bit by claiming to be from a reputed brand or a business.
- Internal parties like employees can be involved in fraud. Barracuda research found that 34% of business owners reportedly said employees would be involved with attackers, and 21% revealed that their employees were behind the fraud.
Social engineering attacks prove that the ‘people factor’ dictates an organization’s approach to cybersecurity practices, processes, and investments in technology. At iTech GRC, we help enterprises maximize IBM OpenPages with Watson to stay ahead of their data privacy, internal risks, and IT governance practices. Our experts help actively manage and mitigate risks that can compromise cybersecurity and safety using the integrated GRC solution.
Contact our teams to learn more about OpenPages’ AI capabilities for managing your end-to-end GRC objectives in the age of GenAI.
