Homomorphic Encryption: Future of Secure Data Processing & Encrypted Computing

Data privacy has evolved alongside technological sophistications and advancements in cybersecurity attacks. Personally identifiable information (PII) gathered by companies have more than one rite of passage to affirm their safety from misuse that could lead to identity theft, fraud, data loss, or nonconsensual tracking and processing. With the increased regulatory interests at the state, federal, and global levels, enterprises are adopting several industry-leading privacy-enhancing computations (PEC) technologies. Homomorphic encryption is one of the most discussed data privacy techniques for minimizing breaches.
Let’s explore why fully homomorphic encryption (FHE) is the future of secure data processing and encrypted computing!
What is Homomorphic Encryption?
According to Gartner’s research on top privacy trends, by 2024, nearly 60% of large organizations will adopt at least one type of PEC method in analytics, business intelligence, and cloud computing. Cryptography and encryption are standard data protection and PEC methods in cybersecurity.
Cryptography protects sensitive information over the internet, data storage systems, networks, and digital transactions by encoding data and algorithms, allowing only authorized users to intercept and access it. Encryption converts data in plaintext to ciphertext using algorithms and keys to make it unreadable for those who do not have the decryption keys.
Homomorphic encryption is integral for storing encrypted data in a public cloud while leveraging the built-in analytics capabilities. Large enterprises can confidently outsource their data to any third-party cloud environment without worrying about threats or non-compliance risks for data processing and analysis.
How Does Homomorphic Encryption Work?
Homomorphic encryption converts data into ciphertexts that can still be analyzed or used for complex mathematical computations while encrypting sensitive data. The term Homomorphic is derived from the Greek words ‘Homo’ and ‘morphe,’ meaning ‘same structure.’ It allows infinite calculations and mathematical operations without decrypting the data.
For example, imagine a sensitive data set is encrypted as a ciphertext and must be multiplied with a plaintext of a specific value when the plaintext is also converted into ciphertext. The two datasets are in uniform formats or homomorphic encrypted for multiplication. The calculation will derive the same value as encryption performed on the two dataset’s original versions. This way, the data stays encrypted throughout the lifecycle without compromising data security and integrity. Homomorphic encryptions are useful across healthcare, IT, banking, and financial services industries where customer data privacy is paramount.
Homomorphic encryptions have been around for a while now. In 2008, Craig Gentry from IBM demonstrated that fully homomorphic encryption was plausible. Gentry’s method described how both additions and multiplication operations could be performed on encrypted data without increasing the noise. Over the years, newer research on homomorphic encryption schemes based on Gentry’s findings has been applied across use cases.
Different Types of Homomorphic Encryptions
Homomorphic encrypted data allows addition, multiplication, or both. There are three types of homomorphic encryptions based on the frequency and type of mathematical operations performed on the ciphertext. They are:
- Partially Homomorphic Encryptions (PHE): The PHE allows only one type of mathematical operation (addition or multiplication) on the encrypted data. It enables performing Additive, Multiplicative, and Comparison Homomorphism unlimited times.
- Fully Homomorphic Encryptions (FHE): FHE is suitable for computationally intense operations on encrypted data without decryption. It allows additive, multiplicative, and Boolean operations (calculations for generating value using AND, OR, NOT, etc).
- Somewhat Homomorphic Encryptions (SHE): Unlike PHE, SHE allows only a limited number of additive and multiplicative computations on encrypted data.
Practical Applications of Homomorphic Encryptions
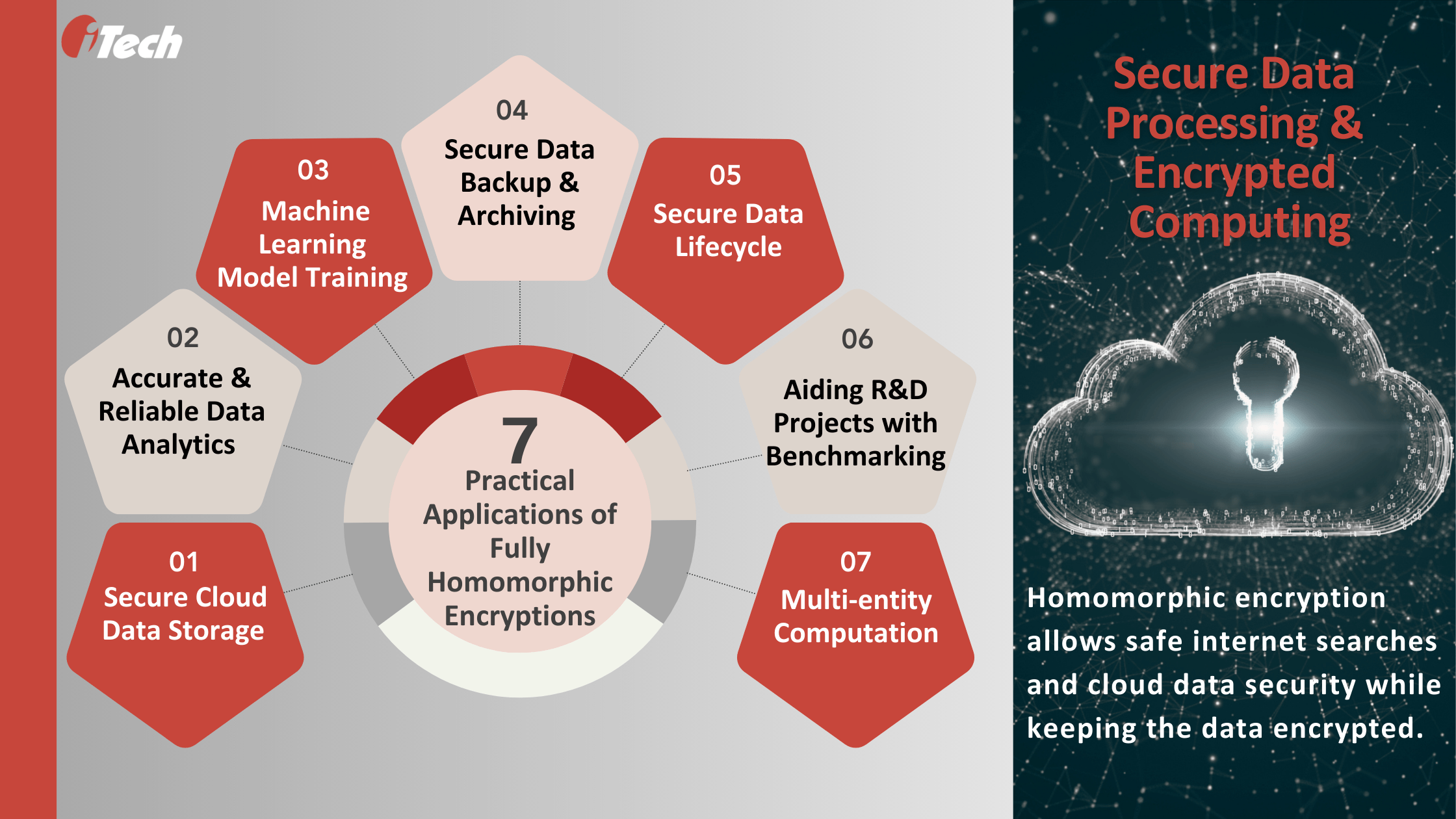
FHE is relevant across digital use cases like running encrypted queries on the search engine, identifying a specific file or data from a remote server using the Boolean constraint, or for secure third-party computation and analysis. The most common uses of FHE include:
- Secure Cloud Data Storage: Large enterprises can leverage FHE to encrypt sensitive financial and banking information, personal information, or confidential national security data to transfer and store them in the cloud computing environment. Without worrying about the confidentiality or risk of unauthorized decryptions, processing securely in the cloud environment and extracting valuable data insights is easy.
- Reliable Data Analytics: Generate reports and insights using descriptive, predictive, prescriptive, or diagnostic analytics while keeping data private and fully encrypted.
- Training Machine Learning Models: Businesses can increase their ML teams to securely train algorithm models on private data while keeping it fully or partially homomorphically encrypted. This enables the training of the ML models using supervised and unsupervised learning.
- Secure Data Backup and Archiving: Encrypted data across storage systems cannot be accessed unless the users have the appropriate homomorphic encryption algorithms to decrypt the data. This makes data storage and backup secure, helping the organization uphold user and customer trust regarding data privacy and protection.
- Secure Data Lifecycle: Homomorphic encryptions maintain data integrity across the data lifecycle, from secure data exchange between authorized entities that have decryption keys to data processing and cleansing without risk of breaches to integration to data warehouse or BI systems. They also aid enterprises in meeting their data governance obligations by overseeing how the data is processed, stored, and exchanged while remaining encrypted.
- Propelling R&D with Secure Benchmarking: Homomorphic encryption is valuable in propelling R&D efforts based on sensitive and confidential data to aid drug discovery or benchmarking for business success. It helps retain intellectual property protection and privacy of highly confidential data while supporting research projects and identifying key statistics and KPIs in encrypted form.
- Multi-entity Computation: A notable benefit of homomorphic encryption is multi-party computation without data manipulation or alteration risk. Encryption keeps the data values unaltered and private through the value chain across third parties and multiple systems.
Conclusion:
In principle, homomorphic encryption adds value across industries like government, defense systems, retail, manufacturing, supply chain, financial services, healthcare, and life sciences. However, it does not guarantee risks from developments in quantum computing. Leading industry stalwarts like IBM, Microsoft, SAP, and others are at the forefront of this disruptive innovation in cybersecurity.
According to GlobalData’s report on Cybersecurity in Technology: Homomorphic Encryption, more than 4.1 million patents have been filed and granted over the last three years. IBM is one of the leading patent filers. The promise of making homomorphic encryption the cybersecurity norm is plausible today as more companies move their data to hybrid multi-cloud environments.
Until then, enterprises can still enforce the zero-trust principle by leveraging the IBM OpenPages Data Privacy Management and IT Governance solutions. iTech GRC’s IBM-certified teams and GRC professionals can guide with assessments of enterprise GRC needs tool evaluation, implementation, module selection, upgrades, and migration to an integrated GRC solution.
Contact our team if you need more insights on making your business risk-resilient while staying data-driven.
